In today’s digital-first world, website security is no longer optional. Cyberattacks are increasing in frequency and sophistication, targeting websites of all sizes—from personal blogs to enterprise platforms. For a professional webdesign agentur, understanding web security vulnerabilities is critical not only to protect client data but also to maintain trust, reputation, and compliance.
This article explains the most common web security vulnerabilities, how they work, why they are dangerous, and how a modern webdesign agentur can prevent them.
Why Web Security Matters for a Webdesign Agentur
A single vulnerability can lead to:
Data breaches
Website defacement
SEO penalties
Loss of customer trust
Legal and financial consequences
Clients today expect secure websites by default. That means every webdesign agentur must embed security best practices into design, development, and deployment—not treat them as an afterthought.
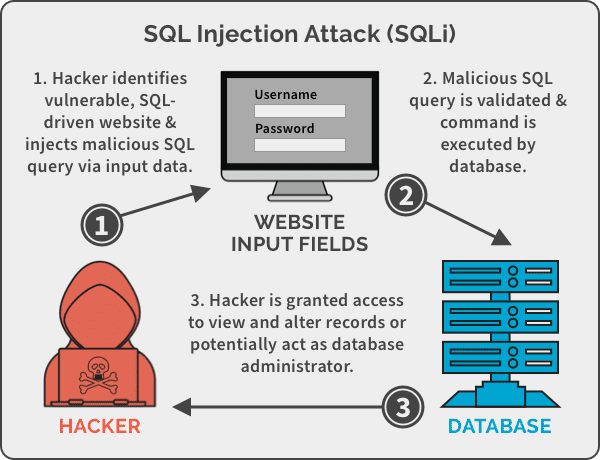
1. SQL Injection (SQLi)
What Is SQL Injection?
SQL Injection occurs when attackers manipulate database queries by injecting malicious SQL code through input fields like login forms or search boxes.
How It Works
If user input is not properly validated, attackers can:
Bypass authentication
Read sensitive data
Modify or delete databases
Example:
Why It’s Dangerous
SQL Injection can expose:
Passwords
Customer data
Payment information
How a Webdesign Agentur Can Prevent It
Use prepared statements and parameterized queries
Validate and sanitize all user inputs
Apply least-privilege access to databases
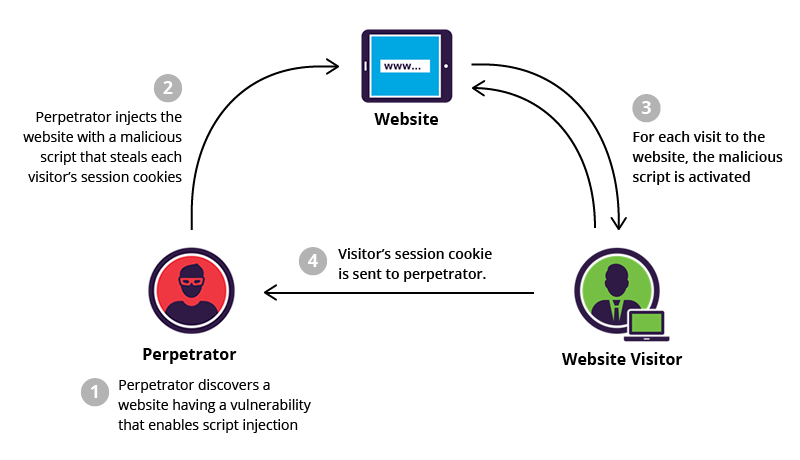
2. Cross-Site Scripting (XSS)
What Is XSS?
Cross-Site Scripting allows attackers to inject malicious JavaScript into web pages viewed by other users.
Types of XSS
Stored XSS – Malicious code stored in the database
Reflected XSS – Script reflected via URLs or form inputs
DOM-based XSS – Executed directly in the browser
Why It’s Dangerous
XSS attacks can:
Steal session cookies
Hijack user accounts
Redirect users to malicious sites
Prevention Tips for a Webdesign Agentur
Escape user-generated content
Use Content Security Policy (CSP)
Avoid inline JavaScript
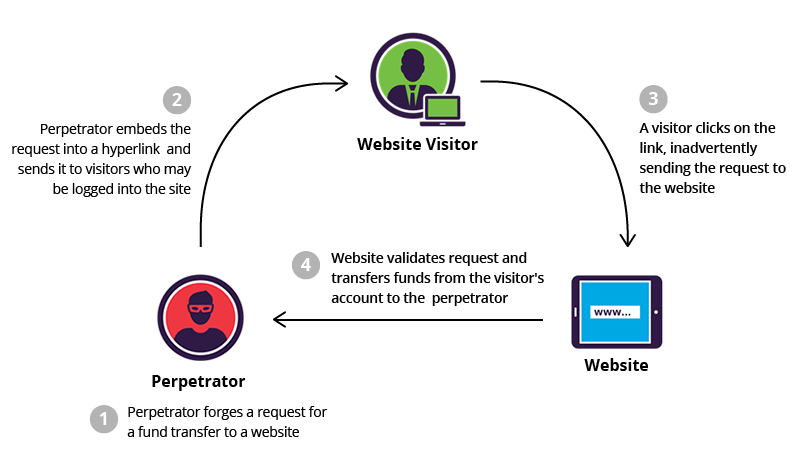
3. Cross-Site Request Forgery (CSRF)
What Is CSRF?
CSRF tricks authenticated users into performing unwanted actions without their knowledge.
Real-World Example
A logged-in user clicks a malicious link that silently:
Changes their password
Transfers funds
Deletes an account
Why It’s Dangerous
The server believes the request is legitimate because it comes from an authenticated session.
How a Webdesign Agentur Can Prevent CSRF
Use CSRF tokens
Implement SameSite cookies
Require re-authentication for sensitive actions
4. Broken Authentication
What Is Broken Authentication?
Occurs when login systems are poorly implemented, allowing attackers to:
Guess passwords
Steal session tokens
Bypass authentication
Common Causes
Weak passwords
No rate limiting
Predictable session IDs
Why It’s Dangerous
Attackers gain full access to user accounts or admin panels.
Best Practices for a Webdesign Agentur
Enforce strong password policies
Enable multi-factor authentication (MFA)
Use secure session management
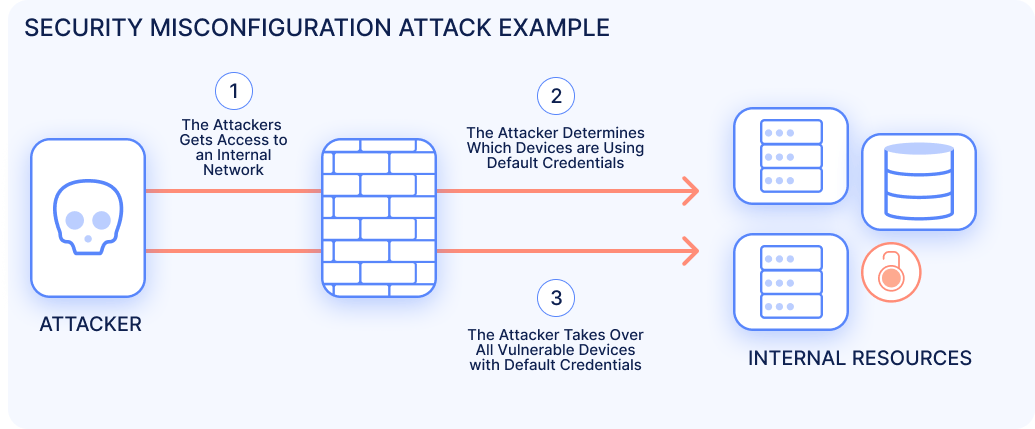
5. Security Misconfiguration
What Is Security Misconfiguration?
Happens when servers, frameworks, or applications are left with default or insecure settings.
Examples
Open admin panels
Unpatched software
Exposed error messages
Why It’s Dangerous
Attackers exploit misconfigurations to gain unauthorized access.
How a Webdesign Agentur Can Avoid This
Disable default credentials
Regularly update software
Hide detailed error messages in production
6. Sensitive Data Exposure
What Is Sensitive Data Exposure?
Occurs when confidential data is transmitted or stored without proper encryption.
Commonly Exposed Data
Passwords
Credit card details
Personal information
Why It’s Dangerous
Leads to identity theft, fraud, and compliance violations.
Security Measures for a Webdesign Agentur
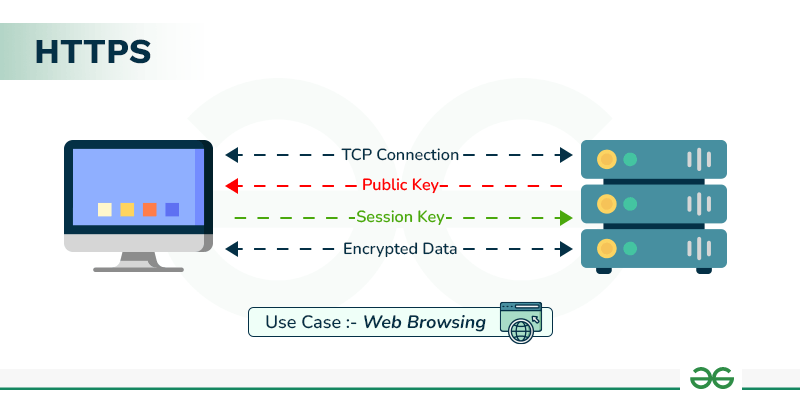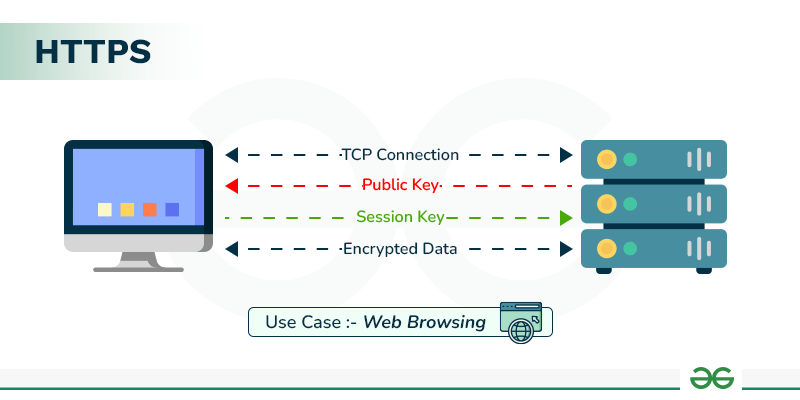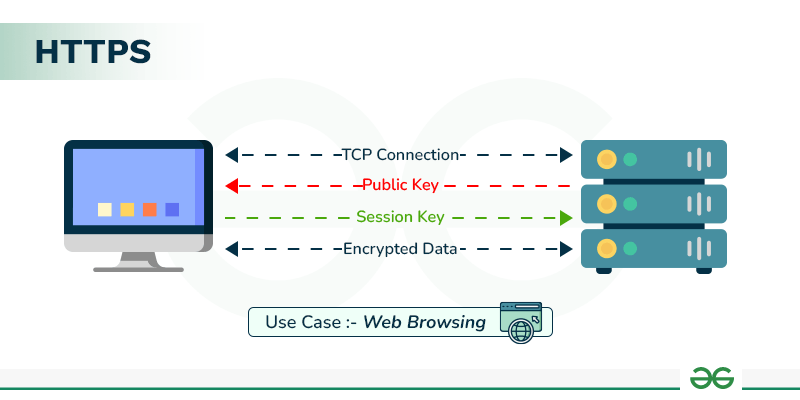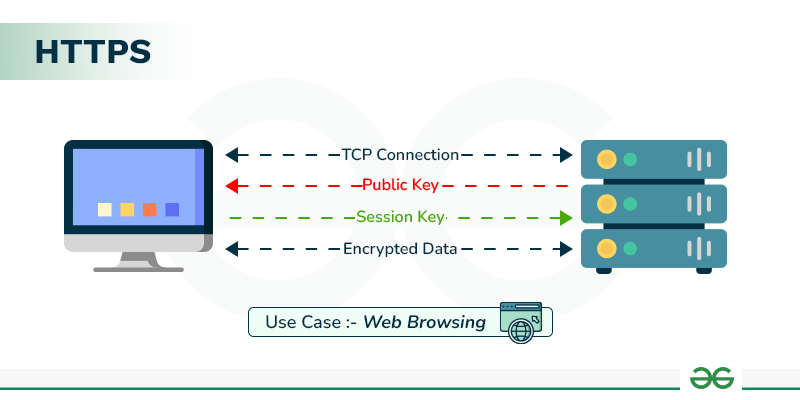
Enforce HTTPS using SSL/TLS
Encrypt data at rest and in transit
Hash passwords using modern algorithms
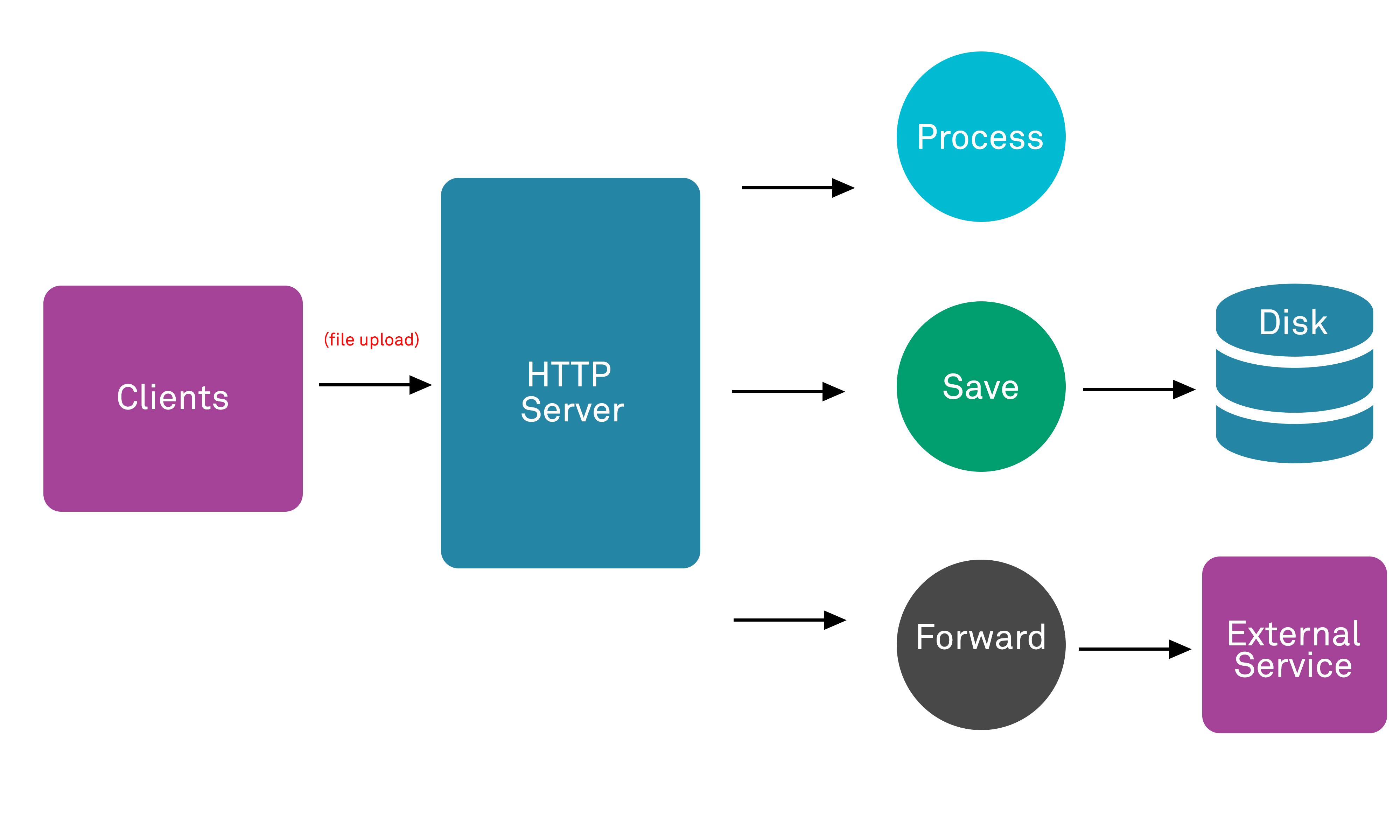
7. File Upload Vulnerabilities
What Are File Upload Vulnerabilities?
When users can upload files without proper validation, attackers may upload:
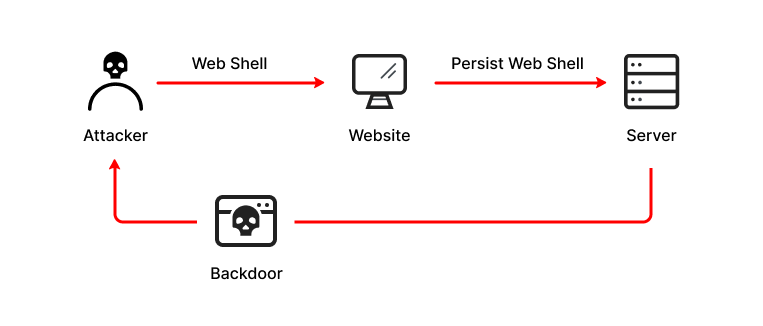
Malware
Web shells
Executable scripts
Why It’s Dangerous
Attackers can gain remote control of the server.
How a Webdesign Agentur Can Secure File Uploads
Restrict file types
Validate MIME types
Store uploads outside the web root
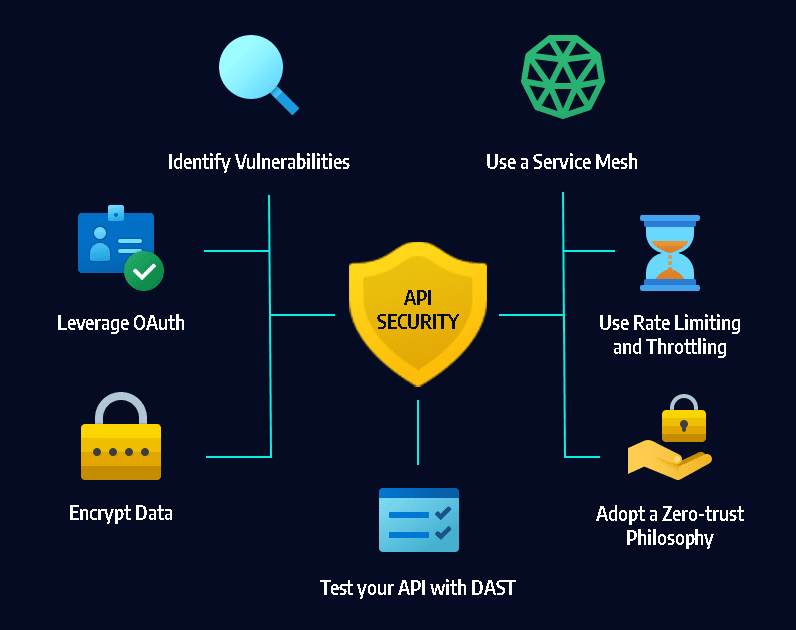
8. Insecure APIs
What Are Insecure APIs?
APIs without proper authentication, authorization, or rate limiting.
Why It’s Dangerous
Attackers can:
Access sensitive data
Abuse endpoints
Perform automated attacks
API Security Tips for a Webdesign Agentur
Use API authentication (OAuth, tokens)
Validate input and output
Implement rate limiting
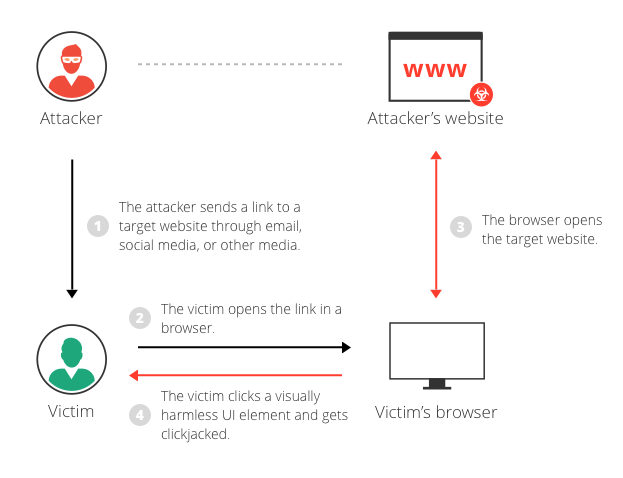
9. Clickjacking
What Is Clickjacking?
Users are tricked into clicking invisible elements layered over legitimate buttons.
Why It’s Dangerous
Users unknowingly authorize actions or reveal information.
Prevention Methods
Use X-Frame-Options headers
Implement Content Security Policy
How a Webdesign Agentur Should Approach Web Security
A modern webdesign agentur should adopt a security-first mindset:
1. Secure by Design
Security should be integrated from the planning stage—not added later.
2. Regular Testing
Vulnerability scanning
Penetration testing
Code reviews
3. Client Education
Explain risks and best practices to clients clearly and proactively.
4. Continuous Updates
Keep frameworks, plugins, and servers up to date.
Conclusion
Web security vulnerabilities are a serious threat—but they are also preventable. From SQL Injection and XSS to insecure APIs and misconfigurations, understanding these risks empowers a webdesign agentur to build safer, more resilient websites.
In an era where trust is everything, security is not just a technical requirement—it’s a competitive advantage. By following best practices and staying informed, every webdesign agentur can protect its clients, reputation, and long-term success.